The Central Government notified the Information Technology (Intermediaries Guidelines) Rules, 2011 in April, 2011. A draft amendment of these Rules has been issued by the Ministry of Electronics and Information Technology (MeitY), ostensibly for dealing with the fake news and misinformation problem. However, the Rules could result in weakening the security and privacy of apps and websites and erode the safe harbour protection available to intermediaries. MeitY is seeking comments to the Draft Rules by 15 January 2019.
This FAQ aims at making these Draft Rules easy to understand and at making various stakeholders aware of the problems with the draft Rules.
Who are Intermediaries?
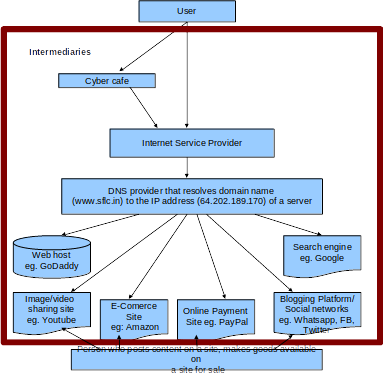
Intermediaries are entities that provide services enabling the delivery of online content to the end user. Let us look at the players involved in this chain:
Internet Service Providers (ISPs) – ISPs like Airtel and MTNL help users to get connected to the Internet by means of wired or wireless connections.
Search engines – These are websites like Google and Bing that help users to search for specific information on the web. They provide links to websites that have content relevant to the search terms given by the user.
DNS providers – These service providers translate the domain names (eg. www.sflc.in) to addresses (e.g. 13.126.242.41) that can be understood by computers.
Web hosts – These are service providers like GoDaddy.com that provide space on servers to place files for various websites so that these sites can be accessed by users.
Interactive websites – This includes social media sites like Facebook and Twitter that act as platforms to store and retrieve content, blogging platforms like Blogspot and Wordpress, auction sites like eBay, and payment gateways like PayPal. The pictorial representation gives an overview of the intermediaries involved in a common Internet transaction.
Cyber Cafes – It means any facility from where access to the Internet is offered by any person in the ordinary course of business to the members of the public. The Information Technology Act, 2000 includes cyber cafes also under the ambit of the definition of intermediaries.
What is Intermediary Liability?
Interactive websites like blogging platforms, messaging apps, social media and e-auction sites host / transmit user-generated content. Cyber cafes, free WiFi providers and telecom companies such as providers of broadband and mobile data act as a mere pipeline for people to access the Internet. Sometimes content posted by users could be illegal, like content infringing on someone's copyright or pornographic content. The intermediaries who host / transmit this content could also be held liable for the content if they do not satisfy the conditions for gaining immunity from such liability laid down by the law.
What is meant by ‘Safe Harbour Protection’?
The intermediaries like telecom service providers, cyber cafes, web hosts, social networking sites and blogging platforms provide important tools and platforms that allow users to access the Internet, host content, share files and transact business. Websites like Blogspot, Youtube and Facebook only provide a platform for users to post their content, and do not have any editorial control over this content.
Governments across the world realised that these intermediaries must be given protection from legal liability that could arise out of illegal content posted by users, considering the importance of these intermediaries in the online space and the fact that their mode of operation was quite different from the traditional brick-and-mortar businesses. Countries like the USA, members of the European Union and India provide protection to intermediaries from such user generated content. Such protection is often termed as a 'safe harbour' protection.
Do Intermediaries enjoy Safe-Harbour Protection in India?
Yes, Section 79 of the Information Technology Act, 2000 gives the intermediaries protection from liabilities that could arise out of any legal action initiated on the basis of user generated content.
The safe harbour protection available to intermediaries is conditional upon their observing “due diligence” while discharging their duties and observing guidelines issued by the Government in this regard.
These guidelines have been issued in the form of the Information Technology (Intermediary Guidelines) Rules, 2011. The Ministry of Electronics and Information Technology is now proposing an amendment of these Rules by issuing the Draft Rules. Under the new draft, the roles and responsibilities of intermediaries will be widened, and in turn, the rights of users will be reduced.
How do the Draft Intermediary Rules Operate?
The new intermediary guidelines, mandate the intermediaries to impose a set of rules and regulations on users like you and me. The terms of such regulations include a broad list of categories of content which should not be posted by users.
Up until March 2015, any person aggrieved by any content on the Internet could ask the intermediaries to take down such content. Intermediaries were obliged to remove access to such content within a period of 36 hours from the time of receipt of the complaint. These provisions were read down by the Hon’ble Supreme Court in Shreya Singhal v Union of India and it was held that content needs to be taken down only when directed by a Court order or by the appropriate Government.
As per the Draft Rules, intermediaries are obliged to take down the content on receipt of a court order or a direction from the Government or an agency of the Government within a period of 24 hours. The intermediaries which do not comply with a take-down order lose safe harbour under the Information Technology Act, 2000.
Rules in a nutshell for Intermediaries:
Do’s
-
Publish Rules / Privacy Policy.
-
Inform users monthly that their services could be terminated if they don’t comply with the Rules and Privacy Policy.
-
Assist Government agencies within 72 hours of receiving request and enable tracing out the originator of unlawful information. An originator is the person that first sent a message, image, audio, video or file.
-
Follow reasonable security practices as prescribed in the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Information) Rules, 2011.
-
For an intermediary with more than 50 lakh users:
-
Incorporate as a Company in India
-
Have a permanent office in India
-
Appoint a nodal person for coordination with Law Enforcement
-
-
On receiving court order/ notification from a Government agency, remove unlawful information within 24 hours.
-
Preserve unlawful information for 180 days or a longer period as required.
-
Deploy automated tools to remove unlawful information.
-
Report cyber security incidents to CERT.IN.
-
Publish name of Grievance Officer.
-
Strictly follow provisions of the IT Act or any other laws in force.
Dont’s
-
Don't knowingly host prohibited content.
-
Don’t initiate transmission, select receiver or modify information.
-
Don’t deploy or install or modify the technical configuration of computer resource which may change or has the potential to change the normal course of operation of the computer resource.
What is the kind of content that is restricted under the Rules?
You cannot host information that is a
-
grossly harmful,
-
harassing,
-
blasphemous,
-
defamatory,
-
obscene,
-
pornographic,
-
paedophilic,
-
libellous,
-
invasive of another's privacy,
-
hateful, or racially, ethnically objectionable,
-
disparaging,
-
relating or encouraging money laundering or gambling,
-
or otherwise unlawful in any manner whatever,
-
harm minors in any way or
-
infringes any patent, trademark, copyright or other proprietary right.
-
violates any law for the time being in force;
-
deceives or misleads the addressee about the origin of such messages or communicates any information which is grossly offensive or menacing in nature;
-
threatens public health or safety; promotion of cigarettes or any other tobacco products or consumption of intoxicant including alcohol and Electronic Nicotine Delivery System (ENDS) & like products that enable nicotine delivery except for the purpose & in the manner and to the extent, as may be approved under the Drugs and Cosmetics Act, 1940 and Rules made thereunder;
-
threatens critical information infrastructure.
These terms are so confusing. Are they defined anywhere?
That's a little complicated! The terms describing unlawful content are very ambiguous and most of these are not defined either in the Rules or in the IT Act, 2000. In fact many of these terms are not defined in any statute.
So, you are saying that we do not know what these terms mean? Doesn't the normal English language meaning apply to them?
The basic principle of law is that it requires certainty. We need to be told exactly what is allowed and what is prohibited in our country. In fact, the Hon’ble Supreme Court had struck down Section 66A of the Information Technology Act, 2000, as the terms used in the provisions were ambiguous and vague. This prohibited list includes terms like defamatory, obscene, harassing or infringes any patent, trademark, copyright or other proprietary right amongst others. These terms can mean different things to different people. What is obscene to a certain set of persons may be art to another. What is defamatory for one person may be political satire for others. Proving infringement of proprietary rights is to be done by the Judiciary with the help of experts and businesses cannot be closed down merely on the basis of suspicion or whims.
We are running a start-up which provides an interactive service to users using a website and an app. Do these Rules affect us?
The Rules will bind all intermediaries as defined by the IT Act, 2000, once it is notified. Rule 3(7) of the Draft Rules mandates that the intermediary shall be a company incorporated under the Companies Act. This is applicable only to those intermediaries that have more than 50 lakh users in India or is in the list specifically notified by the Government. Such companies should also have a permanent registered office in India with a physical address and should appoint a nodal person of contact and an alternate senior functionary for 24 X 7 coordination with law enforcement agencies.
O.K. I am bored and I am not sure if these Rules affect me anyway.
Well! Watch out what you post next time as your status update, as it might offend someone or the automated tool deployed by the intermediary could find the content to be illegal resulting in the intermediary terminating your services. In addition to regulating content the Rules also deal with government's power to access user information from the intermediary.
The Rules mandate intermediaries to cooperate with government agencies and provide information to them for the purpose of verification of identity, or for prevention, detection, investigation, prosecution etc when a request has been made by the agency in writing. This power granted to the Government agencies does not have any system of checks and balances to safeguard the interests of users.
The Rules also mandate the intermediaries to inform the users that their services can be terminated if they violate the terms of service. So you are left to the mercy of the intermediaries. Whether they want you to access the Internet or not is their prerogative, not yours! This provision could have far more serious consequences than the three strikes legislation that has been introduced in countries like France, South Korea and Taiwan.
In short, this will lead to:
-
censorship of content.
-
curtailment of your freedom to express opinions
-
violation of your right to privacy as the intermediaries could be forced to part with user information without any checks and balances.
-
a right for intermediaries to arbitrarily disconnect services of users.
Enough of this technical and legal jargon. Just tell me what can I do.
The Government is accepting comments on these draft Rules till January 15th and Counter comments are accepted till January 28th, 2019. Comments / suggestions may be sent to gccyberlaw[at]meity[dot]gov[dot]in, pkumar[at]meity[dot]gov[dot]in or dhawal[at]gov[dot]in
You could also blog about the Rules, write articles in media and be involved in activities that would raise awareness about the issue.


